Install a ‘BLE scanner’ app on your smartphone and scan. All the weird codes that look like this, 2B:FC:F3:A3:D3:2B, are Bluetooth MAC addresses, emitted by people.
A huge crime has been committed. Our friends and families “have been chipped”.
In the short documentary below, I did a Bluetooth LE scan in an indoor swimming pool to eliminate the chance those MAC addresses could come from phones. If there are no phones, where are the Bluetooth signals coming from? It’s the people.
In the BlueTruth documentary, researchers investigated the phenomenon in May 2022. They pointed out Bluetooth codes are emitted by the COVID-19 vaccinated and nose swabbed. In France the test was repeated too in the Hold On documentary (snippet).
This has been tested over and over again by many, and everbody agrees, this is real. Confirming it for yourself is easy.
Simply install a BLE scanner app and scan in a crowded area, or head out somewhere where there are no people, except those you want to scan. BLE is an abbreviation for Bluetooth Low Energy.
I pumped everything I know in the video below.
Mini Documentary
You can click the title inside the video frame, to jump to the video on Odysee.com. From there, you can download the video by clicking the three dots (…), then click download, done. You can just watch it here too of course.
Odysee | YouTube
You can watch the video above on YouTube at the time of writing (Feb 9 2024), where there are auto-generated subtitles for people who don’t speak English.
I saved those subtitle files, so if you’re handy with videos and want to create a video with subs in your language, go ahead. Available languages in the .zip: en, nl, fr, de, es, it, tr, af, ar, ru.
How to set up your phone for BLE scanning
There are two methods that work independently of each other.
- Enable ‘Show nameless Bluetooth devices’ in developer options (Android).
- Install a BLE scanner app (Android & iPhone).
Forensics so far
People have tried to connect to the BLE implants, sniff (eavesdrop) the Bluetooth wireless traffic, hack them etc. No useful new information came from it whatsoever to my knowledge. The BLE implants are likely secured on a military level, encrypted etc.

Screenshot from Dark City (1998).
Disappearing MAC addresses
People often report MAC addresses disappearing, and wonder what’s going on.
From mainstream Bluetooth LE knowledge, devices turn on and off to preserve energy. When there’s nothing happening or to do, it turns off.
The range of the BLE implants is easily 50 meters (164 feet) in an open space, and about 10 meters (32 feet) inside buildings. Once they’re out of range, you don’t see them anymore in your scanner app.
Some issued the idea the implants detect when there’s a Bluetooth scan happening nearby, and turn off shortly after it notices. I have not yet confirmed that, but deem it possible.
A BLE device that collects data and keeps it on site, is not very useful. It has to send the data over the internet, to a place where the data is collected, analyzed, exploited… Therefore, BLE devices pass on their data to an internet gateway device.
Internet Gateway devices
In the literature involving WBANs, Wireless Body Area Networks, there is talk of gateway devices that serve as a pathway to the internet.
As it often goes with these things, it sounds more complex than it is. Just look at the picture below, and you’ll quickly get it.
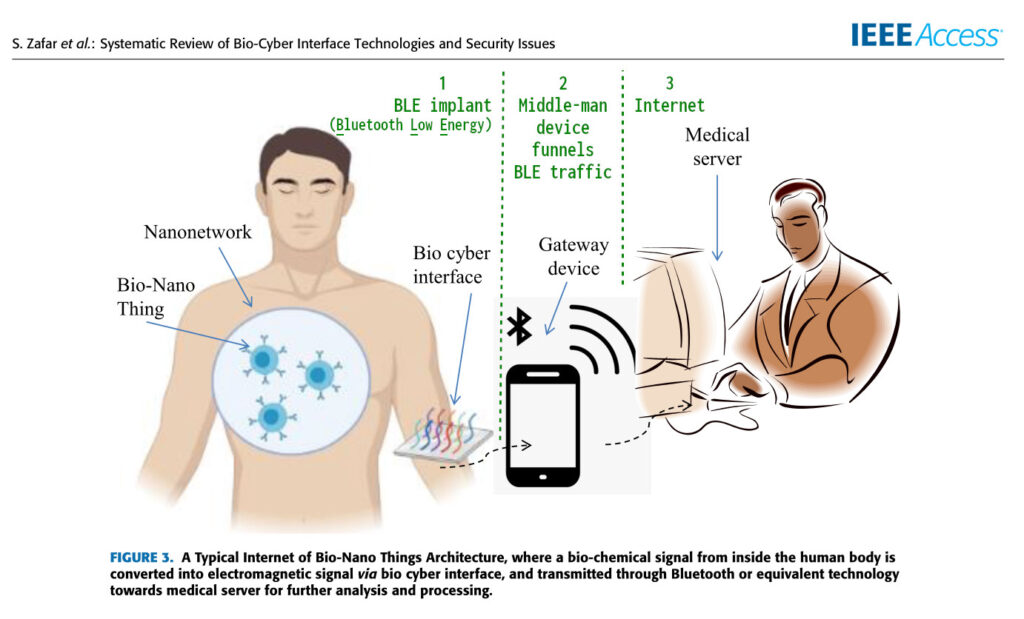
The Bio-Cyber interface in the picture above is a perfect match for the BLE implants that send out MAC addresses.
When a BLE device sees a gateway, it will send its data to it. If it has no new data to send, when it’s all “synced up”, it won’t, to preserve energy.
If a gateway is out of range, a BLE device can pass on its data to nearby BLE devices which forward the data. Just like gossip on a grapevine, the data hops from device to device until it reaches an internet gateway device.
Bluetooth Mesh Networks
A bunch of BLE devices operating in a mesh network, are basically all talking and listening to each other. I think it’s very likely the BLE implants operate in mesh network mode.

Interoperability
I’ve been told all wireless devices are now capable of acting as internet gateways for Bluetooth mesh networks.
Meaning, any phone, iPad, wireless router and maybe even cell towers would funnel through data from the Bluetooth implant mesh networks.
All those devices would be interoperable, compliant to the requirement of interoperability.
I have not confirmed that, but wanted to put out the idea, in case techies want to investigate and prove or disprove it.
Internet of Bodies
Why would anybody do that, people often ask.
In short, to control people with wireless technology. To track, trace, who knows what else.

The Bluetooth implant mesh networks expand the Internet of Things (IoT), with an Internet of Bodies (IoB).
At least, that’s what it looks like to me at the time of writing.
What installs the BLE implant?
COVID-19 injections and swabs.
Actually, all injections are off the table, including dental anesthetics and saline solution.
That’s the only conclusion after considering the microscopy research.
Videos
- Flemming Blicher – Do vaccinated people emit Bluetooth signals?
- Vaxx’d have Bluetooth MAC address (good proof) lady standing on a deck scans swimmers
- Hold On (French documentary, snippet)
- BlueTruth (documentary)
- MAC-cinated: Dr. Luis De Benito on the Bluetooth phenomenon
- David Nixon’s lab vials emitting Bluetooth (1m30s)
- Smoke&Mirrors – Detecting Bluetooth MAC signals at various locations
- Smoke&Mirrors – Bluetooth MAC Codes at under 12’s Rugby Training. What else could it be?
His channel on Bitchute and Odysee - Der Reichsdoktor (Adam Smith) – Bluetooth from beyond the grave 2
- Job and friend scan a graveyard
- WT – The Bluetooth LE Implant System (hypothesis)
- Dr. Richard Delgado – The vaccinated now emit a visible MAC address like a smart phone or WiFi router
- Explanation making use of Mik Andersen’s documents
- FM8 – Broadcast detected in vial of blood
Original source on NextDose.fr, search for title ‘Next Dose 3: Do we still need proof? (anglais)’. - FireMedic8 – Bluetooth criminal complaint filed in Bulgarian police station
- Mat Taylor – Bluetooth Deep-dive anyone? Calling all monkeywrenchers!
- Cronoslogic – Bluetooth People – A Montage of Information
- Cronoslogic – Bluetooth People – My Analysis
- Cronoslogic – Bluetooth People – Drawing Conclusions with the nRF52840 (he could not sniff the BT traffic)
- FireMedic8 – The Scandinavian fetal cell line Bluetooth connection
- BIOTEQ Injectable Microchips – Leaked slides from forgotten USB drive
- WT – Why the MAC addresses changes – MAC address randomization
- WT – Water does not block Bluetooth 2.4 GHz






real
NOT CONFIRMED BY MY EXPERIENCES
Would you care to share how you went about it?
Information like, did you use a BLE scanner app or did you use developer options?
Where did you scan, how many people were around, what did you see?
Greets
https://arxiv.org/pdf/2103.02282.pdf
0x07FF4C0012020000
0x07FF4C0012020001
0x07FF4C0012020002
0x07FF4C0012020003
Have you tried reading the data that is transmitted along with the MAC Address in the Bluetooth LE Advertising Packet? For every person i’ve scanned, they will have one of the 4 hex strings listed above. This packet data and format is almost identical to the data an AirTag transmits when in ‘Nearby State’..
The main differences are;
People won’t have the “Maintained” bit set, but AirTags will, along with battery level data. The last two bytes of the packet will always be 0000 – 0003 for people, and for AirTags it will be 2 bytes of public key data. The MAC Addresses are Resolvable private random addresses, as a security measure, and generally are updated every 15 mins with another MAC generated from the private key.
I use nRF Connect and RaMBLE.. I’ve also used a BLE sniffer with Wireshark to confirm the data i’ve found, including the PDU type;
AirTags – (ADV_IND)
People – (ADV_NONCONN_IND)
https://novelbits.io/bluetooth-low-energy-advertisements-part-1/
**6-12 Months after – They appeared to gain a secondary MAC, this is connectable but returns limited GATT data..
***Since Jan this year there is an exponential increase of yet another MAC, with a unknown identifier 0x1608.. this is not connectable, but has suddenly appeared for a lot of people over last month..
I have not focused much on the advertising packets.
In nRF connect on Android, I have been looking at the information when you fold open a device entry.
It shows things like Device Type, Advertising Type, Flags etc. I suppose that is information from the advertising packet?
I scouted for the four hex codes in that information from a scan at home (neighbors), but I don’t see it.
0x07FF4C0012020000
0x07FF4C0012020001
0x07FF4C0012020002
0x07FF4C0012020003
Maybe I should look at it with Wireshark to see it.
I figured it’s not efficient for me to start learning BLE in depth from scratch, and that a BLE developer or passionate techie would dig into it.
What you commented is very interesting though.
I wonder what the _IND stands for in e.g. ADV_IND.
When you fold open a device entry in the scan list, tap “raw” to see the advertising data.. It should be displayed in a popup..
I use the filter dropdown in the scan list when scanning in large crowds, eg supermarkets.. to display only the people.. You can do this by tapping the filter dropdown, and entering “1202000” in the Advertising Data filter box.. (The filter will append a wildcard *)
I apologize for the messy responses, they only post when i’ve tried posting individual paragraphs, or just changing the wording.. very strange
Don’t worry about the messy responses 🙂
I’ll have to check out everything you wrote and the ‘post comment’ issue later.
I very much appreciate the wealth of knowledge you bring here in regard to Bluetooth scanning skills.
I’ve posted a couple of replies, have they worked?
Oh yes! Thankyou for your response 🙂
When you first install nRF Connect, the newer versions come with the filter preset to hide all Samsung, Apple, Microsoft, Google, and Exposure Notification Devices.. You need to clear this filter (tap the x), otherwise you will not see most devices, or the people because they have the apple manufacturer ID (0x004C)
Here is some explanation of why devices that are not manufactured by apple, will have the apple manufacturer ID in their Bluetooth LE advertising data..
https://stackoverflow.com/questions/43301395/does-an-ibeacon-have-to-use-apples-company-id-if-not-how-to-identify-an-ibeac
“The bottom line is that the exact header (including the company code) must be as specified for iOS to interpret an advertisement as an iBeacon transmission and to return the results using iOS CoreLocation APIs. If a different company code is used, it will simply not be detected by these APIs. Even though different companies manufacture beacons meeting the iBeacon specification, the all use the Apple company code. ”
When you fold open a device entry in the scan list, tap “raw” to see the advertising data.. It should be displayed in a popup..
I use the filter dropdown in the scan list when scanning in large crowds, eg supermarkets.. to display only the people.. You can do this by tapping the filter dropdown, and entering “1202000” in the Advertising Data filter box.. (The filter will append a wildcard *)
If you only use “1202” you will also see AirTags and AirPods as they also use this manufacturer data ID, however the proceeding bytes will be unique, and not “0000”, “0001”, “0002” or “0003”
If you use “0215” in the filter, you will see all iBeacon compatible devices..
To explain the PDU types I mentioned before:
ADV_IND (Connectable Scannable Undirected Advertising): This is the standard type of undirected advertising where the device is discoverable and connectable. Any device can scan for this type of advertising and attempt to establish a connection.
ADV_NONCONN_IND (Non-Connectable Non-Scannable Undirected Advertising): This type of advertising is used when a device wants to broadcast information to all devices around it, but doesn’t want any device to connect to it or scan its advertising data.
Please let me know if you have any other questions I might be able to help with..
I appreciate you considering this information and trying it out for yourself, and very keen to hear about any results or information you find!
To explain the PDU types I mentioned before:
ADV_IND (Connectable Scannable Undirected Advertising): This is the standard type of undirected advertising where the device is discoverable and connectable. Any device can scan for this type of advertising and attempt to establish a connection.
ADV_NONCONN_IND (Non-Connectable Non-Scannable Undirected Advertising): This type of advertising is used when a device wants to broadcast information to all devices around it, but doesn’t want any device to connect to it or scan its advertising data.
Please let me know if you have any other questions I might be able to help with..
I appreciate you considering this information and trying it out for yourself, and very keen to hear about any results or information you find!
When you first install nRF Connect, the newer versions come with the filter preset to hide all Samsung, Apple, Microsoft, Google, and Exposure Notification Devices.. You need to clear this filter (tap the x), otherwise you will not see most devices, or the people because they have the apple manufacturer ID (0x004C)
Just additional info:
I use RaMBLE for wardriving, it was discontinued from app store in 2019, but you will find it.. It’s perfect because it will continue scanning with screen off(!), and you can export the scan history (along with GPS data) to a sqlite file.. The app also has a wide selection of built in filter types, and a mapping feature.. The location data is based upon where you are scanning from, however it does update the precision using additional detection events.. This is really good for locating fixed beacons while driving around.. All the traffic lights here have had a iBeacon upgrade for about a year now.. We unfortunately had a very high uptake here mate.. And errryone and errrything has BLE.. From the cops tasers, to people’s water bottles (lmao)